Microsoft Defender for Cloud Apps (MDCA) Integration for SaaS Discovery
Set up an integration with Microsoft Defender for Cloud Apps to streamline the discovery of your SaaS applications.
Introduction
Note
We're currently experiencing a known issue with the API endpoint
/api/v1/discovery/discovered_appsused for the integration, which is preventing the retrieval of all applications.Responses from the endpoint are paginated, and we face difficulties fetching all applications due to a persistent internal server error (HTTP status code 500) that occurs after the 21000 index. This error indicates an unknown or unhandled internal server issue on the MDCA side.
Despite our best efforts, this issue persists and impacts only a small fraction of our enterprise customers. Over time, we expect to retrieve all applications, as the sorting in the responses appears random and we make multiple requests for the same data. However, we cannot guarantee there will be no gaps in the discovered data via the MDCA integration. We appreciate your patience and understanding as we work towards a resolution.
Microsoft Defender for Cloud Apps (MDCA) is Microsoft's cross-platform solution that offers visibility, control, and protection for cloud applications.
- It provides insights into cloud app usage and risks.
- It enforces policies to prevent data leakage.
- It identifies and combats cyber threats to secure cloud applications.
Because of these capabilities, it can be used to identify and catalog all SaaS applications in use, providing visibility into shadow IT and unauthorized app usage.
Note
If you intend to manually review and link each discovered application to fact sheets, deactivate automatic linking in the SaaS discovery inbox settings before configuring the integration. For details, see Automatic Linking.
Implementation Details
Users provide SAP LeanIX with credentials that have the correct permissions to connect with the integration. Once connected, SAP LeanIX periodically pulls data from the Microsoft Defender API for the discovered applications, specifically calling the /api/v1/discovery/discovered_apps/ endpoint.
Note
The Defender API is only partially documented by Microsoft, and the endpoint used by the SaaS discovery feature is undocumented.
SAP LeanIX has permission to only read applications within Microsoft Defender. Applications are added to Cloud Apps in MS Defender when someone accesses a cloud application through their browser, which could lead to a significant number of discovered applications. To learn more, see Microsoft's documentation Set up Cloud Discovery and Discover and Manage Shadow IT. If you want to cross-check the discovered services, you can do so by navigating to security.microsoft.com and checking the Cloud discovery reports under Cloud apps.
For usage adoption metrics, the count of total active unique users in MDCA is determined by the configured stream in your system and what you have defined as a time window in MDCA.
| Integration Categories | Authentication Mechanism | API Endpoints Used |
|---|---|---|
| Cloud Access Security Brokers (CASB) | REST API - OAuth | For API authentication: /<tenantID>/oauth2/v2.0/tokenFor SaaS discovery: /api/v1/discovery/discovered_apps |
Discovery Capabilities
| Available capabilities | Description | MDCA resource |
|---|---|---|
| SaaS Discovery (Standard) | SaaS discovery automatically identifies your organization's SaaS applications. | Discovered Apps |
| Usage Indication (Optional) | Provides insights into how users in your organization access applications. This helps you make informed decisions about adding discovered applications to the inventory. | Active Users (Over the past month) |
You get the following information about the discovered SaaS:
| Field | Description |
|---|---|
| External Category | |
| Description | Description of the SaaS. |
| Organization | Indicates the parent company. |
| HQ Location | The country/region of the provider's headquarters. |
| Supports SAML | Indicates whether the application supports SAML as a sign-on mode. |
| Active Users* | Number of users using an application in the last 30 days. |
| Sanctioned State | Indicates whether an application is approved and safe (Sanctioned) or prohibited and unwanted apps (Unsanctioned) |
| IP Addresses Count | Indicates how many IP addresses have accessed this application. |
| Upload Bytes | Information about the total amount of traffic (in MB) uploaded by the device over the selected period of time. |
| Download Bytes | Information about the total amount of traffic (in MB) downloaded by the device over the selected period of time. |
| Total Bytes | Information about the total amount of traffic (in MB) over the selected period of time. |
| Total Events | |
| Blocked Events | |
| Revised Total Security Score | The revised total security score is a measure of the security posture of your applications and systems. It is calculated based on various factors, such as the number of applications scanned, the number of threats detected, and the number of threats removed. A higher revised total security score indicates that your applications and systems are more secure. |
| First Used | Indicates when the app was first used. |
| Last Modified | Indicates the date and time when the application's metadata was last updated. This includes information such as the application name, publisher, version, file path, and more. If you notice that an application's last modified date has changed, you should investigate the application to determine if it has been modified by malware or if it is simply being updated by the application's publisher. |
| TID | |
| Stream ID |
*Shown only if you enable Usage Indication capability in the configuration settings. To learn how, see Enter the Copied Credentials in SAP LeanIX.
Setting up Microsoft Entra ID Integration
Register SAP LeanIX in Microsoft Entra ID
- Based on the region, sign in to either the Global Azure portal or the China Azure portal. Use the Azure administrator account that is also a member of the Global Administrator directory role in your Microsoft Entra ID tenant.
- On the left navigation pane, click Microsoft Entra ID.
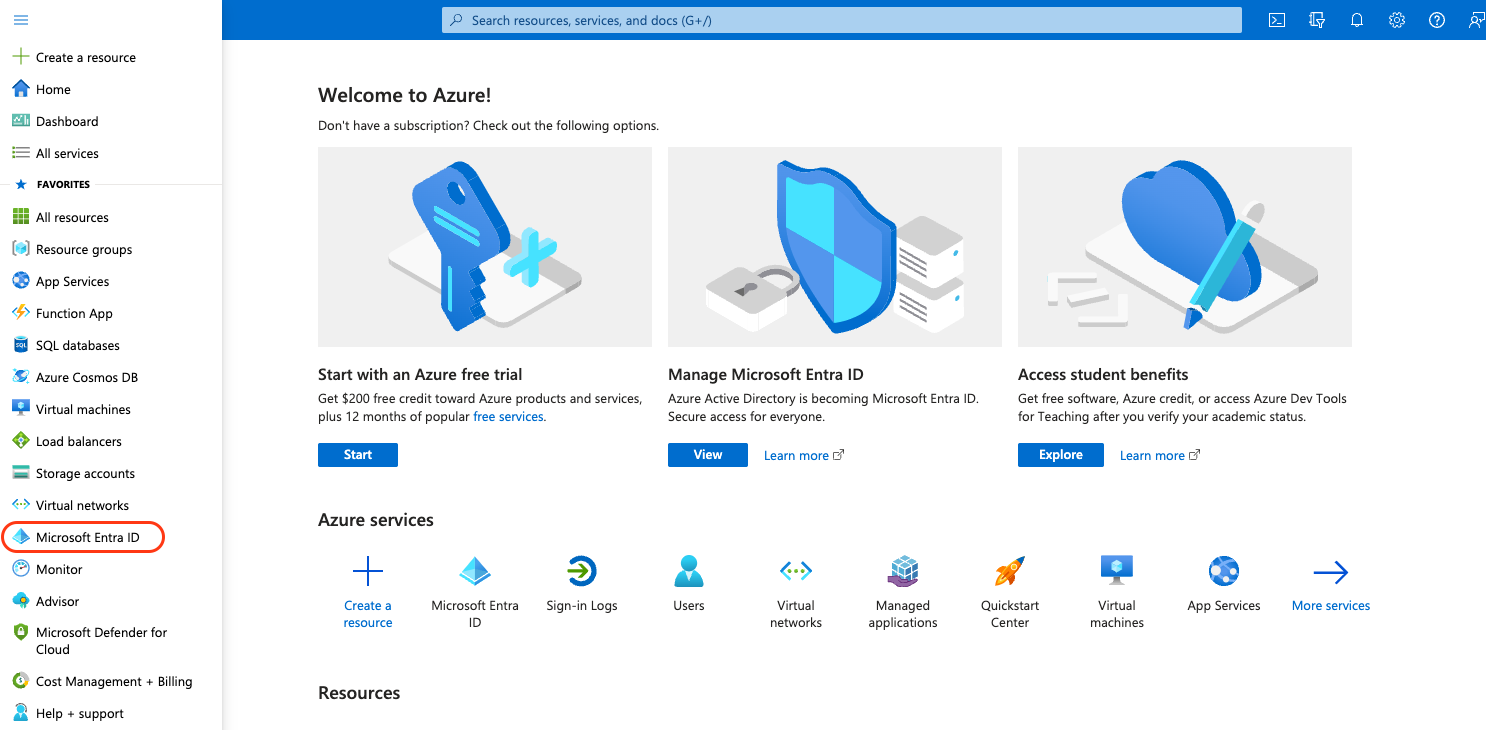
Azure Portal
- On the Microsoft Entra ID page, click App Registrations.
- On the app registrations page, in the toolbar on the top, click New registration.
- In the resulting page, do the following:
- Enter a name for the integration.
- Under Supported account types, select Accounts in this organizational directory only (Default Directory only - Single tenant).
- Click Register at the bottom of the screen.
Grant Permissions to SAP LeanIX
After registering SAP LeanIX, the next step is to grant the necessary permissions to call APIs. Note that only the administrator in MDCA has full access and visibility to the settings and can provide the API URL.
-
On the left pane, click API permissions.
-
Click Add a permission.
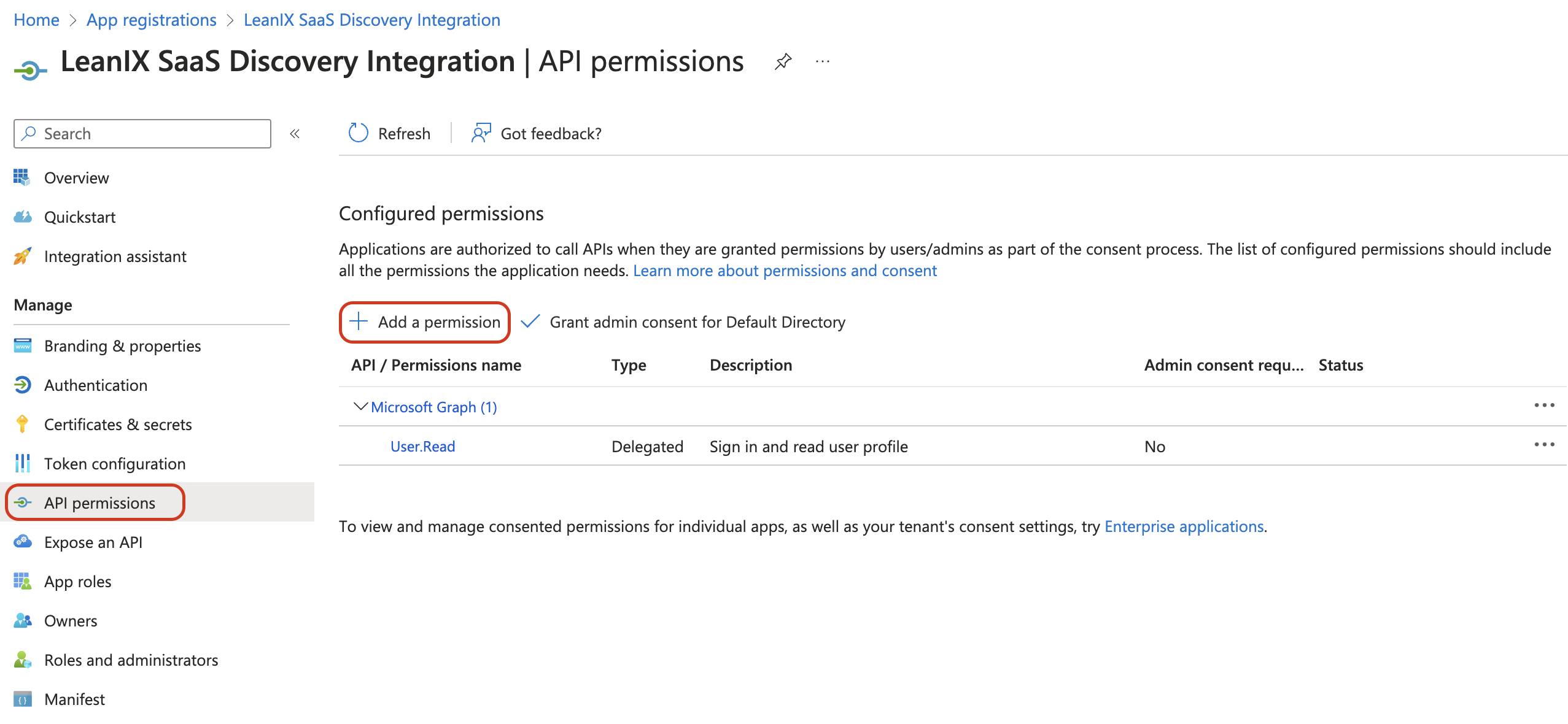
Granting API Permission
-
In the overlay for requesting API permissions, open the APIs my organization uses tab, then search and select Microsoft Cloud App Security API.
-
Select Application permissions at the top and select discovery.read permission from the list below.
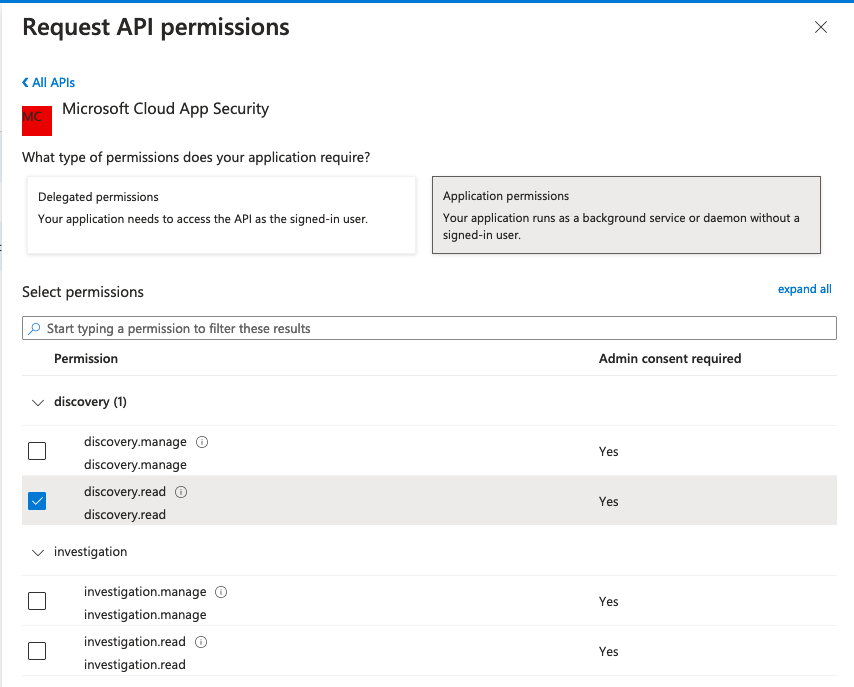
Request API Permission
- Click Add permissions at the bottom to assign permission to SAP LeanIX.
- On the API permissions page, click Grant admin consent for Default Directory to enable configured permissions.
- Click Yes and grant consent for the requested permissions.
- The permission status indicator in the API permissions page will change to approved.
Gather Configuration Settings
-
Return to the application overview section (App registrations > Created app) and gather the following identifiers: Application (client) ID and Directory (tenant) ID.
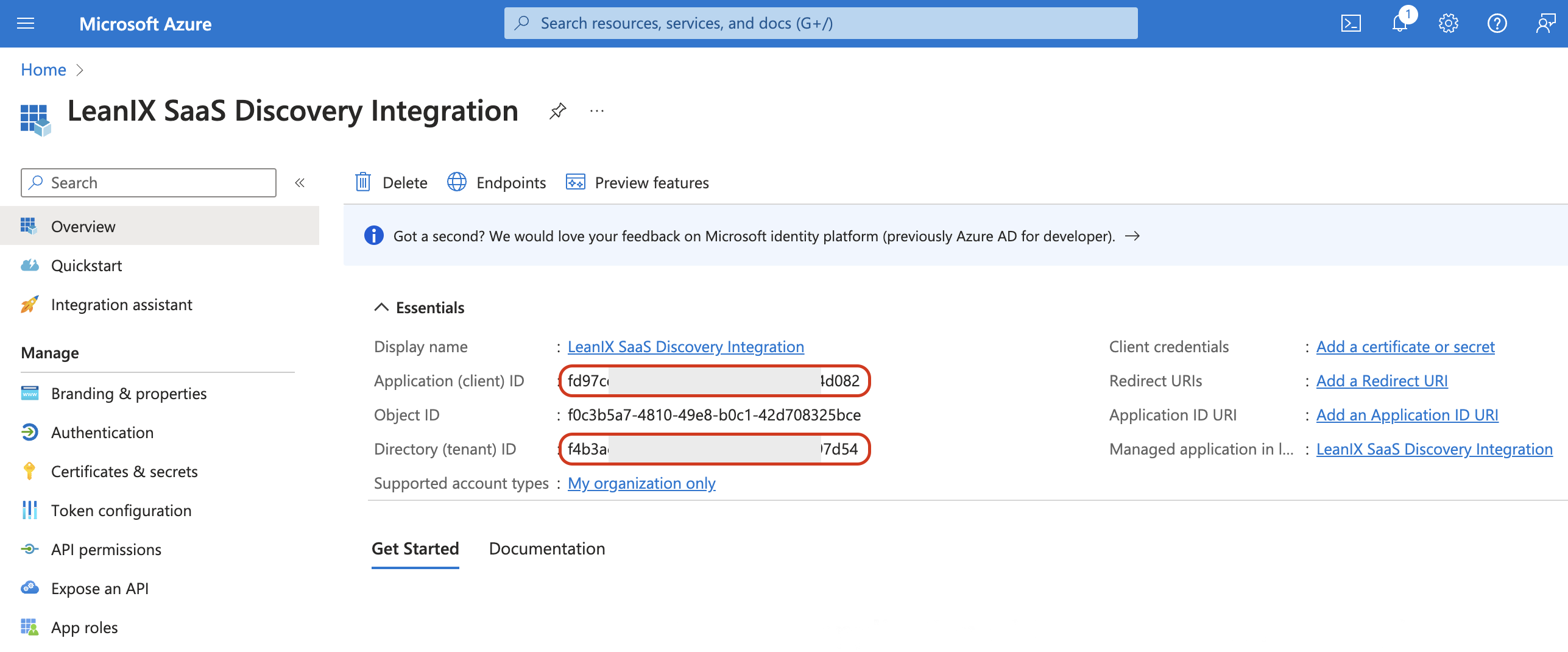
-
From the left pane, open the Certificates & secrets section. Here, generate a client secret (also called the application password) by following these steps:
-
Click New client secret to create a new password.
-
Optionally, enter a description for the client secret.
-
Select the expiration length of the secret. Once the expiration date of the created client secret is reached, you need to create a new one and reconfigure the integration in SAP LeanIX.
-
Click Add.
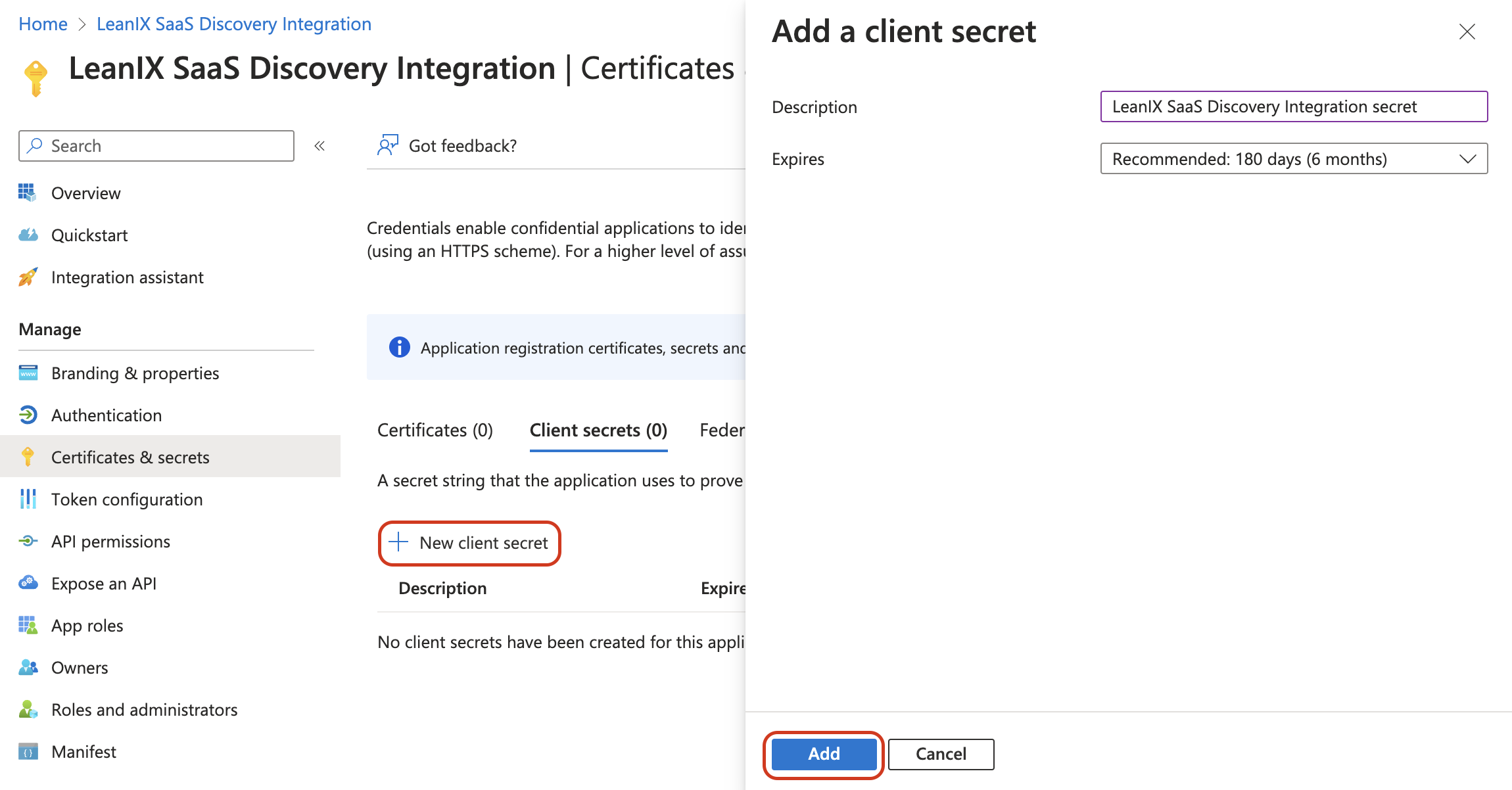
Adding a Client Secret
-
-
Copy the client secret value to your clipboard.
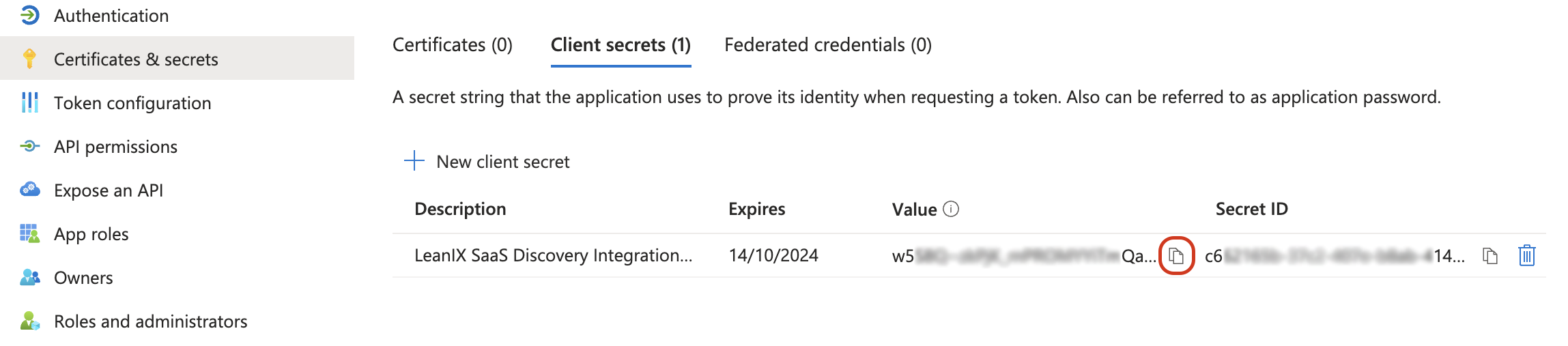
Copying the Client Secret Value
-
Go to the MDCA product, navigate to Settings > Cloud Apps > System > About, and copy the API URL value.
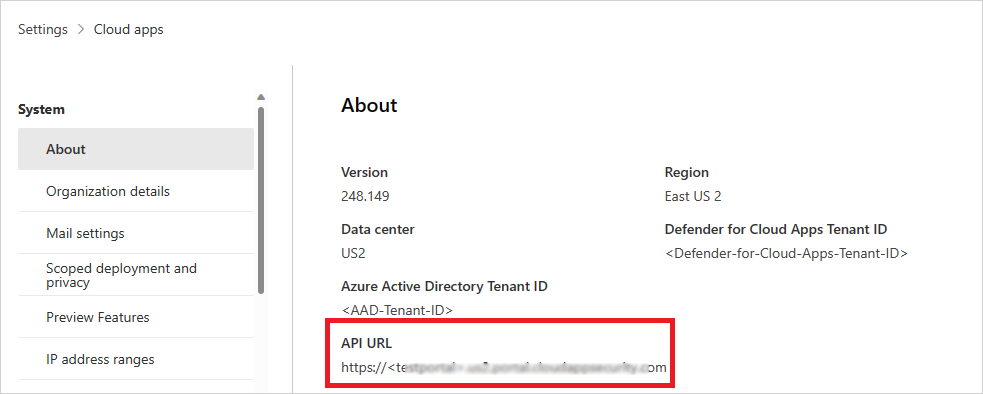
Copying the API URL Value
Enter the Copied Credentials in SAP LeanIX
-
Add the MDCA integration in SAP LeanIX. For more, see Setting-up Out-of-the-Box Integrations.
-
In the configuration, choose a name for the integration and the type of capabilities or data you want to get from MDCA.
-
Enter the credentials copied from the Azure admin portal into the corresponding fields.
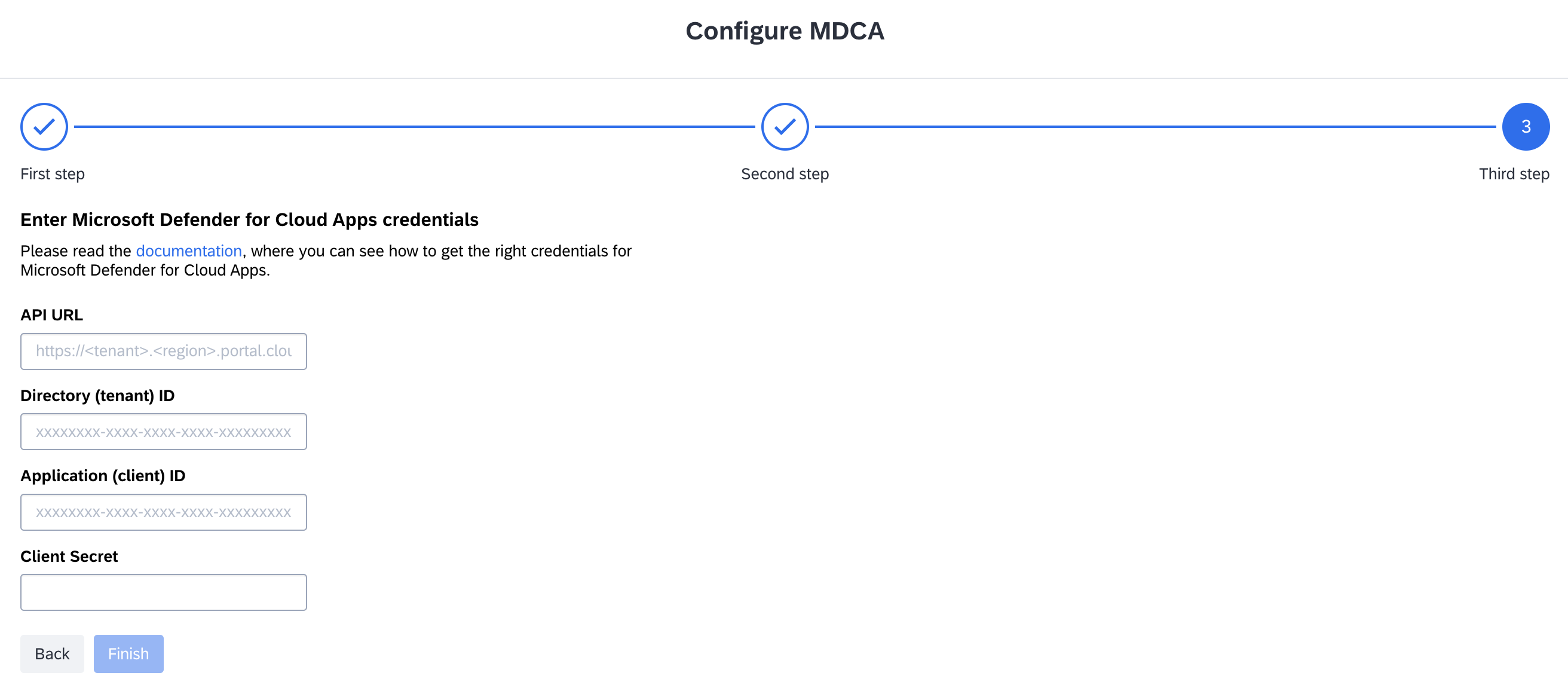
Entering the Required Credentials in SAP LeanIX
-
Click Finish and wait for the connection to be established.
Updated about 1 month ago
