SBOM Discovery from Build Artifacts
Set up automated discovery of SBOMs in your GitHub Enterprise Server instance and seamlessly send them to SAP LeanIX for further processing.
The GitHub Enterprise Server integration supports automatic detection and processing of Software Bill of Materials (SBOMs) generated within GitHub Actions workflows. The integration sends SBOMs to SAP LeanIX for further processing, accelerating the discovery of microservices and improving visibility.
By automating SBOM discovery and linking to SAP LeanIX, the integration eliminates manual efforts, speeding up microservices and tech stack discovery.
Prerequisites
- Set up the integration with GitHub Enterprise Server. For instructions, see GitHub Enterprise Integration.
- Generate SBOMs using your preferred method. For more information, see Generating SBOMs.
- Adopt the SBOM naming convention. Artifacts that don’t follow this convention are not detected. For details, see SBOM Naming Convention.
Configuration
In your GitHub Enterprise Server instance, do the following:
-
Generate and store SBOMs as build artifacts using GitHub Actions workflows. The integration detects SBOMs stored in the build artifacts of workflow runs. For details, refer to the GitHub documentation.
-
(Optional) Select branches to ingest SBOMs from. By default, your repository’s default branch is used.
-
On the GitHub integration page, click the three-dot icon in the upper-right corner > Configure SBOM Discovery.
-
In the overlay that appears, select specific branches or define rules for branch naming. For details, see Branches.
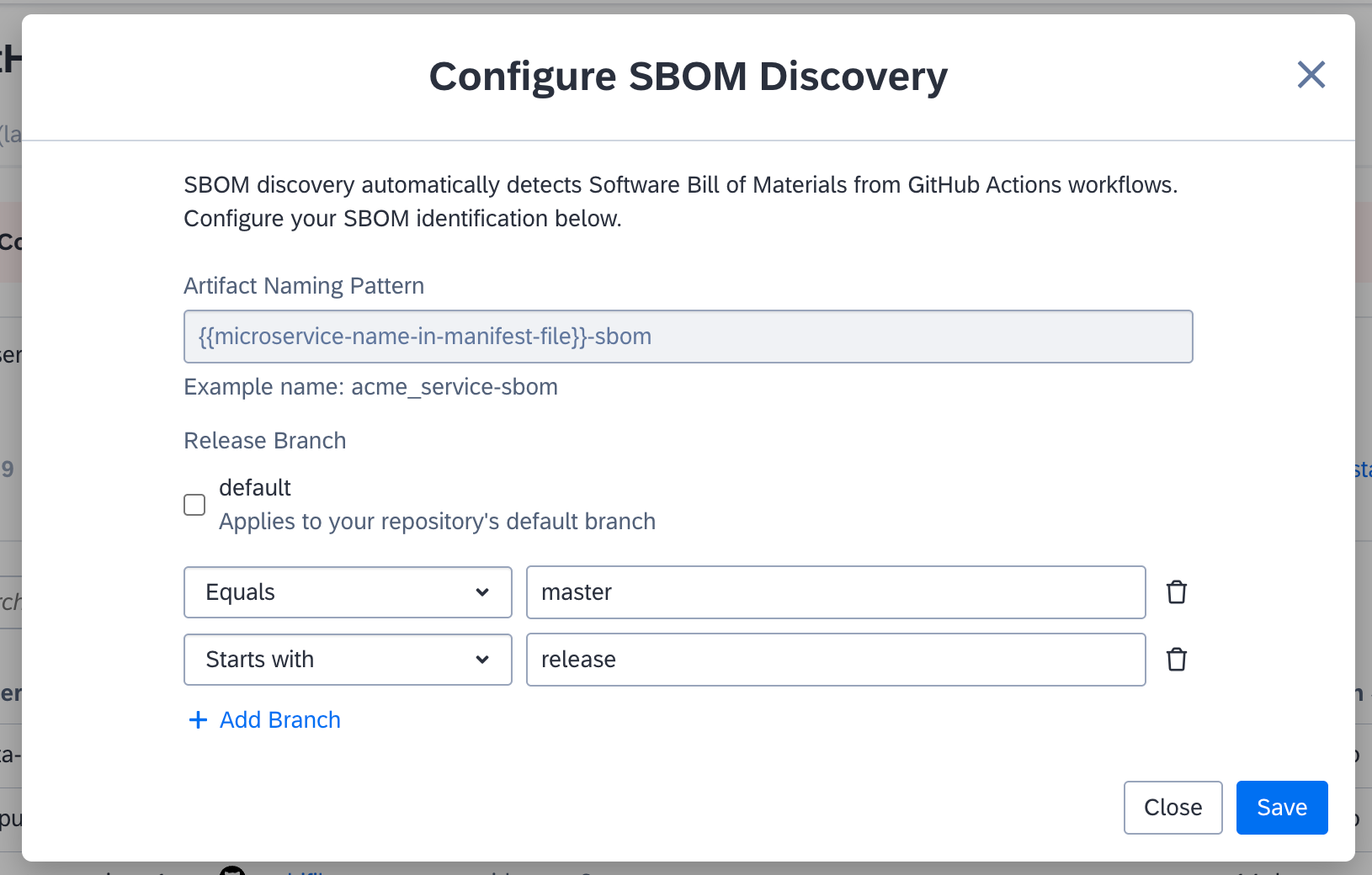
Configuring Branch Rules for SBOM Discovery
-
Once successfully configured, ingested SBOMs appear on the GitHub integration page. The number of SBOMs is displayed under Automated SBOM Coverage.
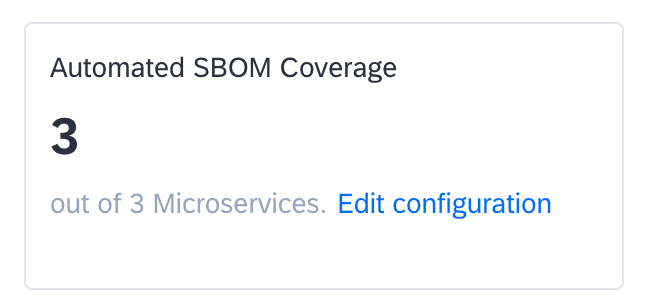
Discovered SBOMs on the GitHub Integration Page
SBOM Naming Convention
The default naming convention for SBOMs must follow the below format:
<microservice-name-as-in-the-manifest>-sbom
- Supported characters include:
- Alphanumeric symbols
- Special characters: dash (-), underscore (_), and slash (/)
- Regular expressions are not supported.
For example, the file name of the SBOM artifact for the ai-assistant microservice is ai-assistant-sbom.
Branches
SBOMs are ingested as build artifacts from the branches you configure in the integration. You can use both the default branch and other branches for this purpose.
- Default branch: This is the repository's default branch, which is set in the repository settings to a branch such as
master,main, ordevelop. By default, SBOMs are ingested from this branch without requiring additional configuration. - Other branches: You can specify particular branch names or define rules for branch naming, such as those that start with
releaseor containversion. In this scenario, SBOMs are ingested from all branches that match the specified criteria.
GitHub App Permissions
To enable the GitHub App to read workflows, subscribe to the workflow_run webhook event. For more details on the required permissions, see GitHub App Permissions.
Example
The following example demonstrates how to generate and store an SBOM using Syft within a GitHub Actions workflow after containerizing a service. You can replace Syft with any SBOM tool of your choice.
The image below shows an SBOM file generated by a GitHub Actions workflow.
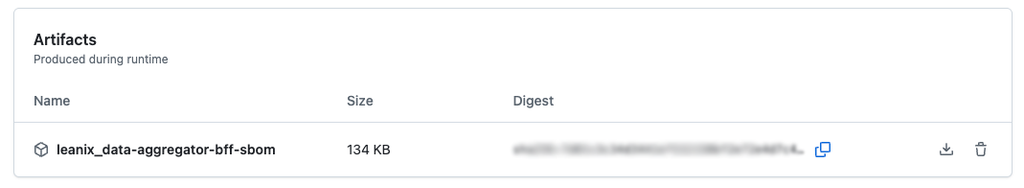
SBOM File Generated by a GitHub Actions Workflow
Recommendation
Add this workflow to a centrally used GitHub Action, such as a compliance action or a post-build workflow, where container images are stored in the registry. This minimizes the effort required by involved teams, ideally limiting the task to the platform team. This setup ensures SBOMs are systematically generated and uploaded as artifacts, allowing seamless processing by SAP LeanIX.
Sample workflow:
name: Generate SBOM for Container Image
description: 'Generate a Software Bill of Materials (SBOM) for a container image using Syft'
inputs:
image:
description: 'The image to generate the SBOM for'
required: true
package_name:
description: 'The name of the package'
required: true
package_version:
description: 'The version of the package'
required: true
sbom_format:
description: 'The file format of the SBOM [default: cyclonedx-json] (available formats: https://github.com/anchore/syft?tab=readme-ov-file#output-formats)'
required: false
default: 'cyclonedx-json'
runs:
using: 'composite'
steps:
- name: Pull the Container Image
shell: bash
run: docker pull ${{ inputs.image }}
- name: Derive SBOM artifact name
id: derive-artifact-name
shell: bash
run: |
echo "SBOM_ARTIFACT_NAME=$(echo "${{ inputs.package_name }}-sbom" | sed 's/\//_/g')" >> $GITHUB_OUTPUT
echo "SBOM_DIR=./sbom" >> $GITHUB_OUTPUT
- name: Download Syft and generate the SBOM
shell: bash
env:
SYFT_FORMAT_SPDX_JSON_PRETTY: "true"
SYFT_JAVASCRIPT_INCLUDE_DEV_DEPENDENCIES: "false"
run: |
curl -sSfL https://raw.githubusercontent.com/anchore/syft/main/install.sh | sh -s --
./bin/syft --version
./bin/syft ${{ inputs.image }} \
--scope "all-layers" \
--source-name "${{ inputs.package_name }}" \
--source-version "${{ inputs.package_version }}" \
--output "${{ inputs.sbom_format }}=${{ steps.derive-artifact-name.outputs.SBOM_DIR }}/${{ steps.derive-artifact-name.outputs.SBOM_ARTIFACT_NAME }}"
- name: Upload SBOM
uses: actions/upload-artifact@v4
with:
name: ${{ steps.derive-artifact-name.outputs.SBOM_ARTIFACT_NAME }}
path: ${{ steps.derive-artifact-name.outputs.SBOM_DIR }}
Updated 30 days ago
