Configuring SCIM in Okta
Instructions for configuring SCIM provisioning in Okta. SCIM allows you to enable seamless and automated user management across your applications.
Prerequisites
Before you start, do the following:
- Learn about the SCIM configuration process in Configuring SCIM.
- Configure single sign-on (SSO) with Okta as an identity provider (IdP). For instructions, see Configuring SSO with Okta.
- Get a long-lived access token through the MTM API. For instructions, see Get a Long-Lived Access Token.
Configuring User Provisioning
Follow these steps:
-
In the Okta admin dashboard, in the Applications section, select the SSO application for SAP LeanIX.
-
On the General tab, in the App Settings section, click Edit, then select SCIM against Provisioning. Save the changes.
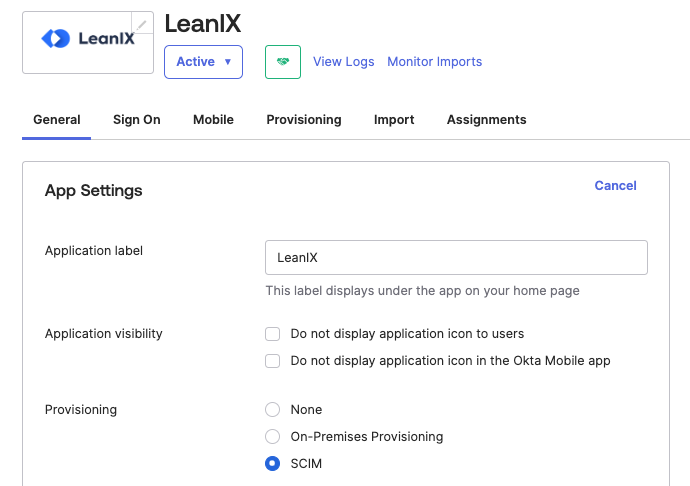
Selecting the SCIM Option for Provisioning in Okta
-
If you've previously created the
roleattribute, in the Profile Editor section, delete the attribute and then recreate it with the following External namespace value. Save the changes. The update might take some time. To verify that the property update has been completed, check a sample user assignment for their role inheritance.urn:ietf:params:scim:schemas:extension:workspacePermission:2.0:User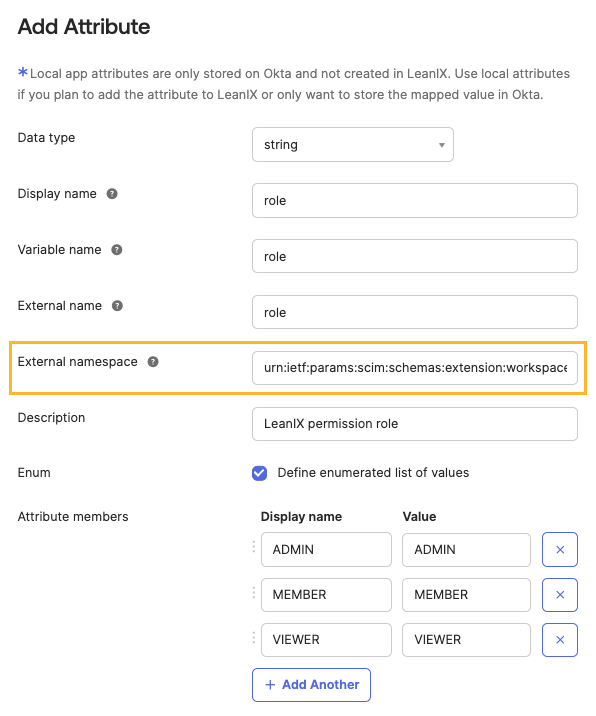
Creating the "role" Attribute
-
On the SSO application page, navigate to the Provisioning tab. In the Integration section, click Edit against SCIM Connection and specify the following details. Save the changes.
Parameter Value SCIM connector base URL https://{SUBDOMAIN}.leanix.net/services/mtm/v1/scim/v2Unique identifier field for users userNameSupported provisioning actions Select the following checkboxes:
- Import New Users and Profile Updates: Any potential changes only apply to users assigned to the SAML application in Okta. If you leave this checkbox unselected, new users assigned to the SAML application won't be created in SAP LeanIX, and any potential changes made to user attributes won't be synchronized.
- Push New Users
- Push Profile UpdatesAuthentication Mode HTTP Header Authorization Long-lived access token that you obtained 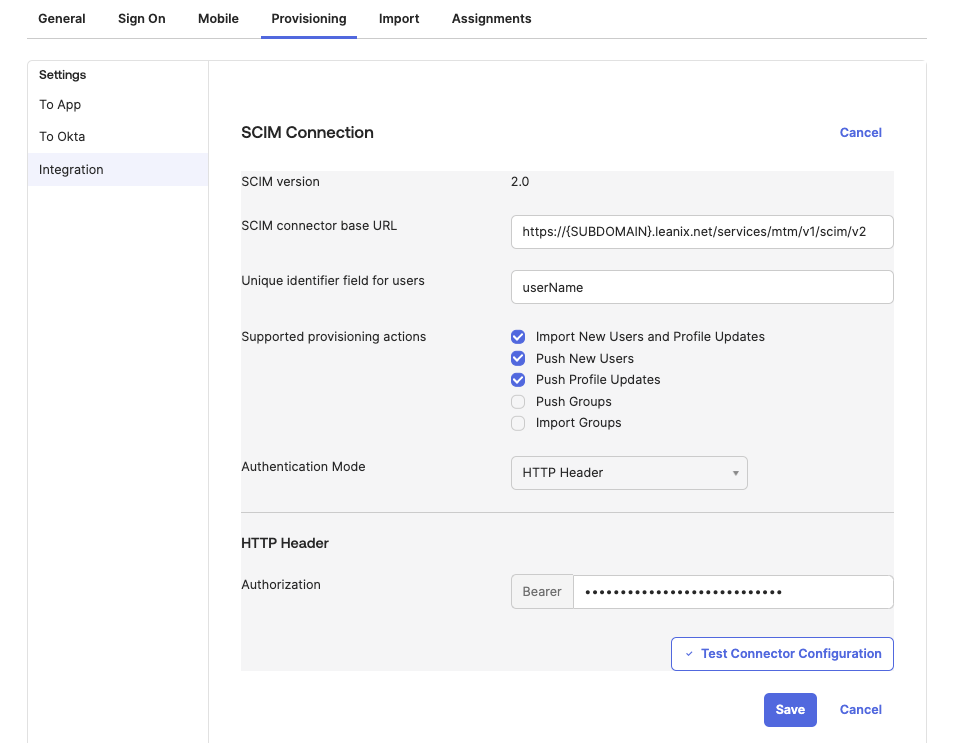
Configuring SCIM Connection Settings
-
On the Provisioning tab, in the To App section, enable the following options:
- Create Users
- Update User Attributes
- Deactivate Users
Save the changes.
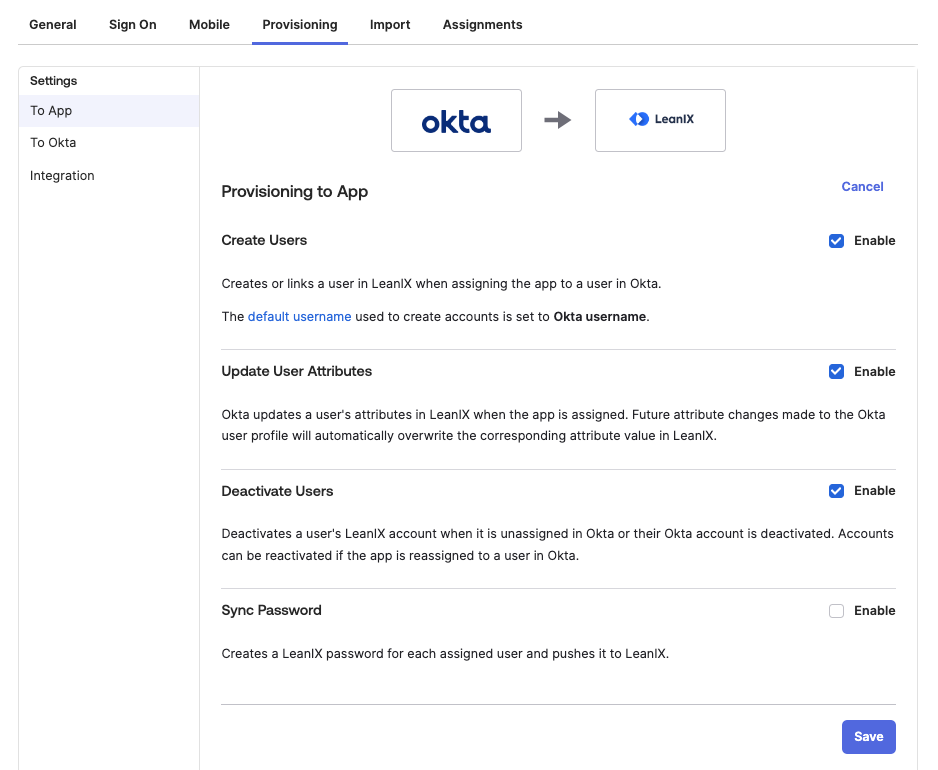
Configuring Provisioning to App Settings
-
To configure attribute mappings, scroll down to the Attribute Mappings section. The following attributes are mandatory for SCIM:
- Username
- Given name
- Family name
- Primary email type
- role: This attribute is only relevant for customers using an external IdP for SSO.
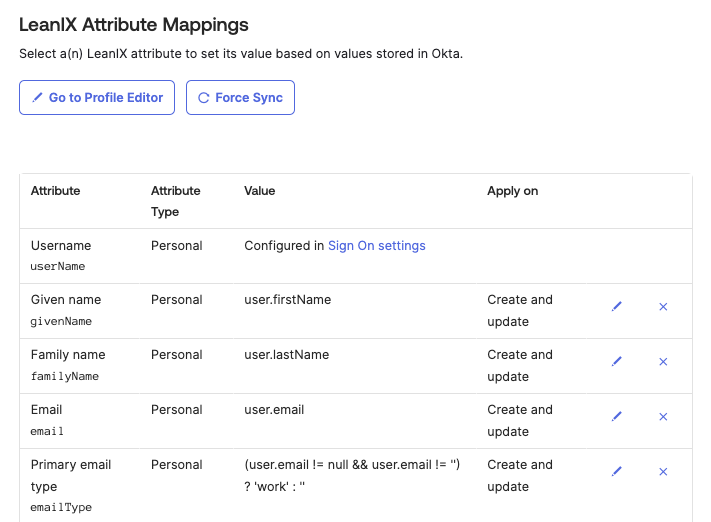
Configuring Attribute Mappings for SCIM
SCIM with Okta is set up. User states should be synchronized between the systems.
Updated 9 months ago
