SBOM Explorer
The SBOM explorer helps you understand your open-source libraries' usage, manage them, track them during cybersecurity incidents, and quickly take action to address risks and compliance issues.
Introduction
The SBOM explorer helps you understand and manage the open-source libraries used in your organization. It also helps you effectively manage dependencies, reduce risks, ensure compliance, and improve software development and IT operations. Currently, the SBOM explorer is available to admins and members.
With the software bill of materials view, you can:
- Understand open-source usage: Understand how open-source libraries are used across your organization's IT infrastructure, including which microservices depend on them, which applications they support, etc.
- Track affected parts during cybersecurity incidents: Quickly identify which parts of your IT system are impacted during cybersecurity incidents, like the log4shell vulnerability.
- Formulate immediate risk mitigation initiatives: Take swift action to address vulnerabilities, for example, by prioritizing updates or patches to affected components.
SBOM Explorer
Using the SBOM Explorer
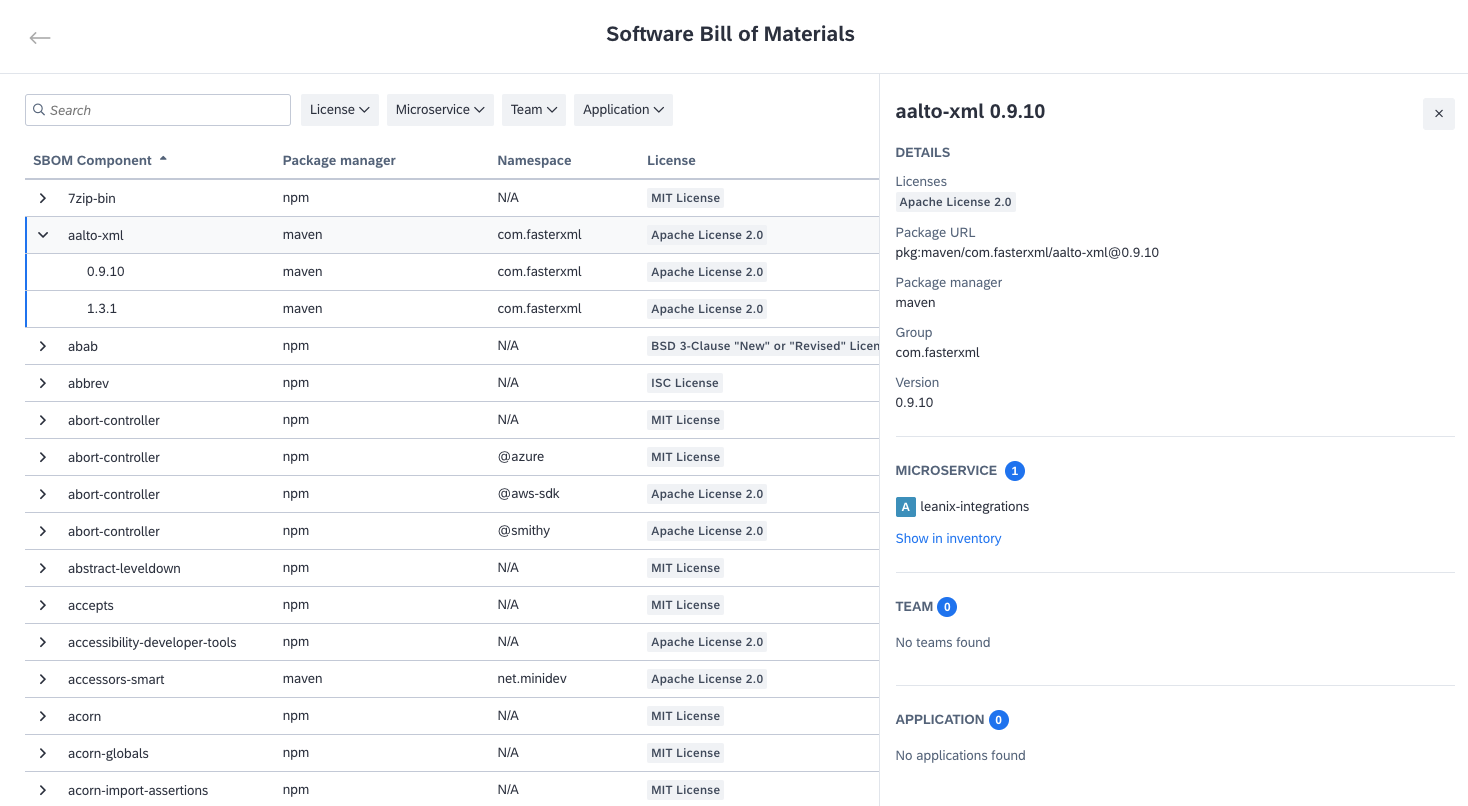
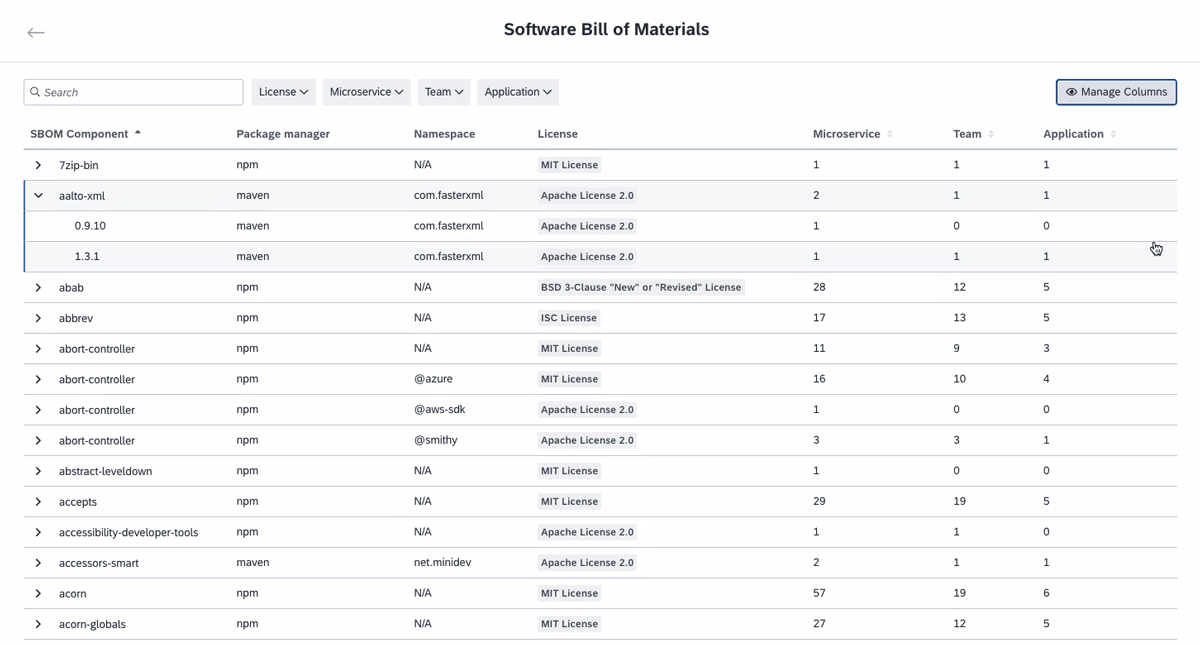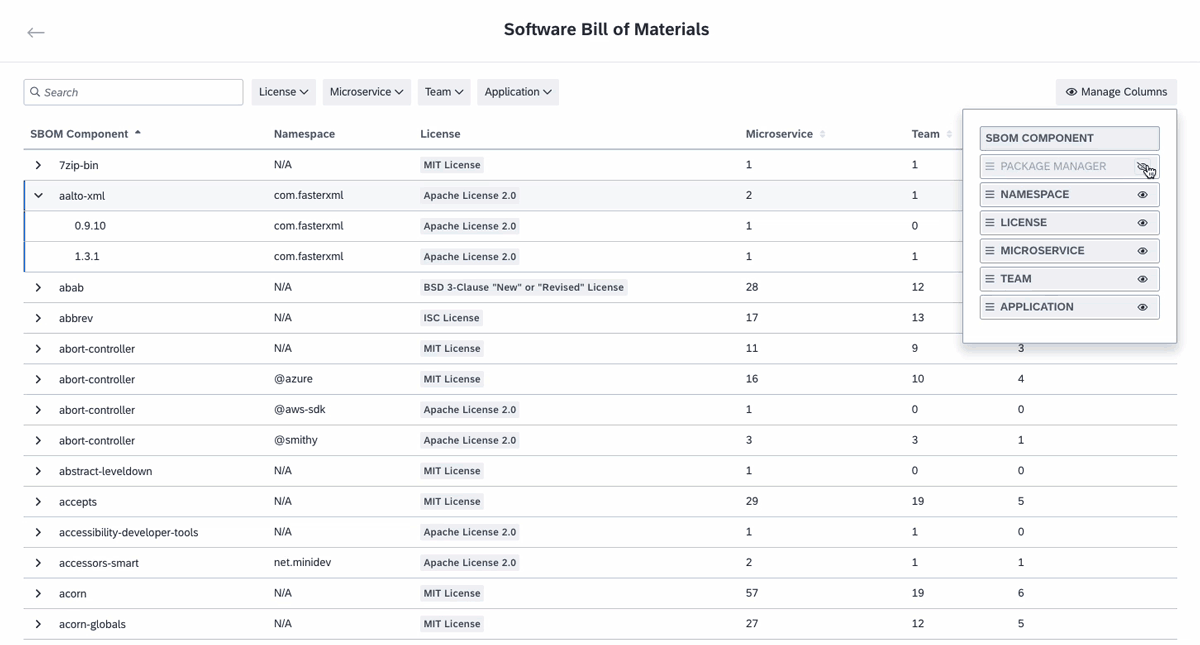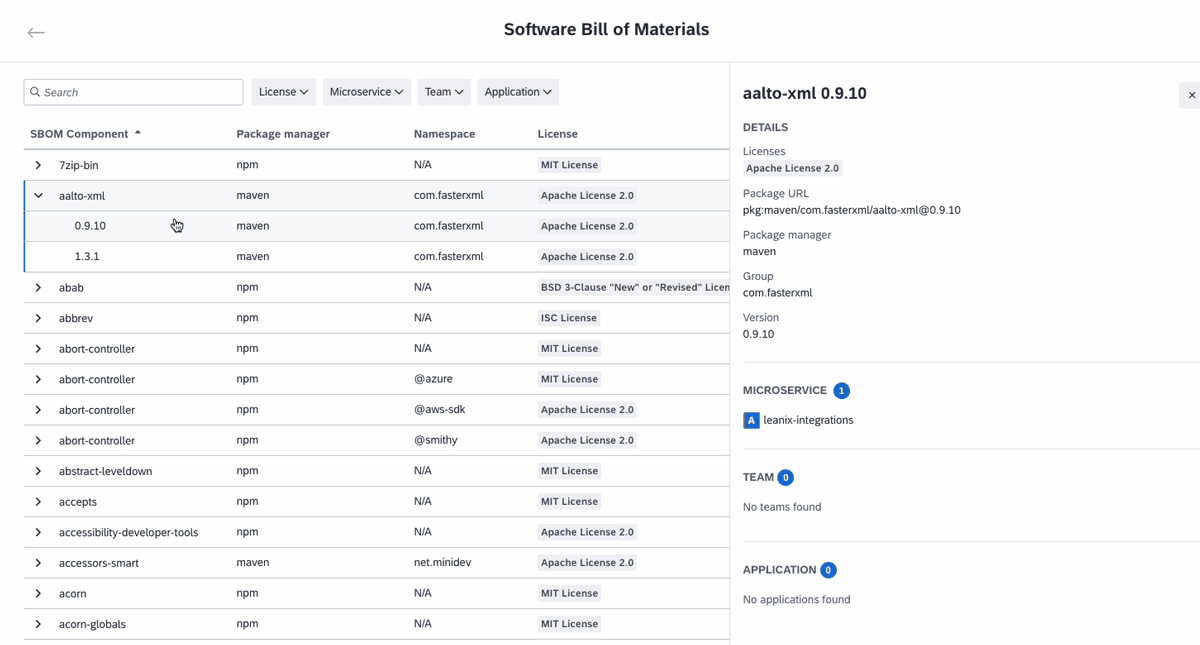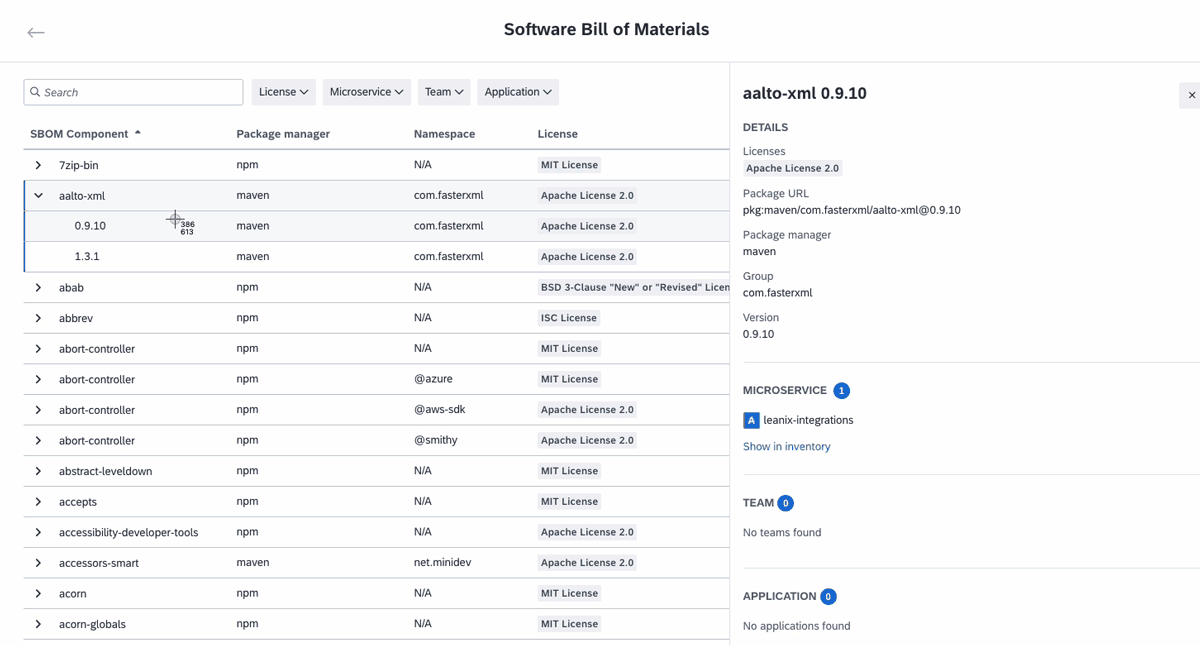
To access the SBOM explorer, navigate to the right-side pane of the inventory and click on Software Bill of Materials. Here, you find a list of all open-source libraries identified across your IT landscape. You can search within this list, apply filters from the drop-down menu at the top, and sort the columns by clicking on the column titles. For example, using the filter function, you can assess license risks by filtering for unpermitted licenses or quickly locate items with known risks through the search function.
Select any item in the list to expand the row and view its sub-components. Clicking on an item opens a pane on the right, providing more details such as license information, version specifics, dependent microservices, associated teams, related applications, and more. This allows you to quickly assess the blast radius and identify which parts of your IT system are at risk during cybersecurity incidents. You can filter items by package manager and namespace, enabling you to view the use of components company-wide and plan your roadmap.
Using the SBOM Explorer
Updated 4 months ago
